
The Different Types of Malware Explained: Viruses, Worms, Trojans, etc.
Understanding the threats to your devices.

Zero Logic Space
Cybersecurity & Online Privacy Watch
Malware Protection & Antivirus Guides
SHARE
The Different Types of Malware Explained
Understanding Viruses, Worms, Trojans, and More

In today's interconnected world, navigating the digital landscape requires an understanding of the potential dangers that lurk online. Among the most pervasive threats is malware, a catch-all term for malicious software designed to harm, exploit, or gain unauthorized access to computer systems and data. Often, the terms "virus," "worm," and "trojan" are used interchangeably, but each represents a distinct type of malware with its own characteristics and methods of attack. To effectively protect yourself and your devices, it's crucial to understand the nuances of these digital threats. This post will explain the different types of malware, detailing how they operate, spread, and what you can do to stay safe.
What Exactly is Malware?
Malware is short for "malicious software." It's any software specifically designed to cause damage to a single computer, server, or computer network, or to steal data or otherwise interfere with normal operations. Cybercriminals use malware for various purposes, including financial gain, espionage, political disruption, or simply to cause chaos.
Malware can infiltrate systems through various vectors, such as malicious email attachments, infected websites, compromised software downloads, external storage devices, and even through vulnerabilities in legitimate software. Once inside, malware can perform a range of harmful actions depending on its type and purpose. Understanding these different types is the first step in recognizing and defending against them.
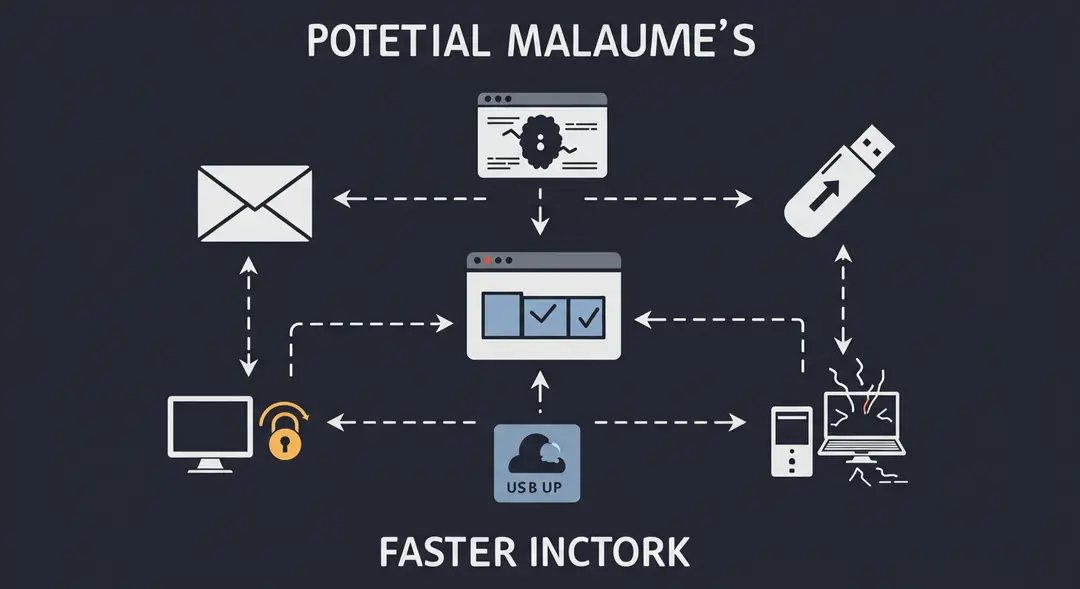
Viruses: The Self-Replicators
Computer viruses are perhaps the most well-known type of malware. Much like biological viruses, they require a host program to spread. A computer virus is a piece of code that inserts itself into another legitimate program or document. When the host program is executed, the virus code runs as well, replicating itself and infecting other files on the system or network.
Viruses often require some form of user interaction to spread, such as opening an infected email attachment, running a compromised executable file, or clicking on a malicious link. Their payload, or the malicious action they perform, can vary widely, from simply displaying annoying messages to corrupting or deleting files, stealing data, or even taking control of the infected system. The key characteristic of a virus is its reliance on a host to propagate.
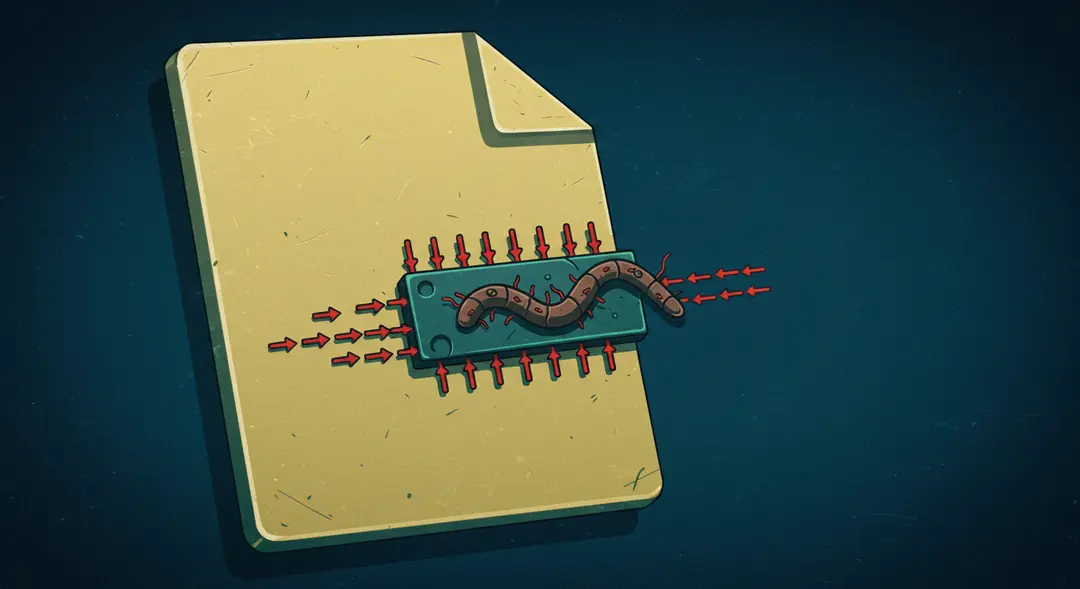
Worms: The Autonomous Spreaders
Unlike viruses, worms are standalone malware programs that can self-replicate and spread independently without needing to attach themselves to a host program or requiring user interaction to propagate. Worms often exploit vulnerabilities in operating systems or software applications to spread rapidly across networks.
Once a worm infects a system, it can create copies of itself and send them to other computers on the network, often consuming significant network bandwidth and system resources, which can slow down or even crash systems. Worms are notorious for their ability to spread quickly and widely, making them particularly dangerous in networked environments. Their payloads can include installing backdoors for remote access, launching denial-of-service attacks, or dropping other types of malware onto infected systems.

Trojans: The Deceivers
Named after the legendary Greek wooden horse, a Trojan horse (or simply "Trojan") is a type of malware that disguises itself as legitimate, desirable, or harmless software or files to trick users into downloading and executing it. Trojans do not self-replicate like viruses or worms. Their success relies on social engineering and deceiving the user.
Once a Trojan is installed and executed, it can perform a variety of malicious actions depending on its programming. Common Trojan payloads include creating a "backdoor" that allows attackers remote access to the infected system, stealing sensitive data (like login credentials or financial information), deleting or modifying files, or downloading and installing other malware onto the system. Because they appear legitimate, users often unknowingly grant Trojans the necessary permissions to operate.

Other Common Malware Types
While viruses, worms, and trojans are some of the most well-known, the malware landscape is vast and constantly evolving. Here are a few other common types you should be aware of:
Ransomware: This type of malware encrypts a victim's files or locks down their system, demanding a ransom payment (usually in cryptocurrency) in exchange for the decryption key or access restoration.
Spyware: Spyware secretly monitors user activity, collecting sensitive information like keystrokes, Browse history, login credentials, and personal data without the user's knowledge or consent.
Adware: While often more annoying than directly malicious, adware displays unwanted advertisements, often in the form of pop-ups or banners, and can sometimes collect user data for targeted advertising. Some aggressive forms can significantly impact system performance.
Rootkits: Rootkits are designed to gain unauthorized "root-level" or administrative access to a system while simultaneously hiding their presence, allowing attackers to maintain persistent control and execute malicious commands undetected.
Conclusion
Understanding the different types of malware is a crucial step in protecting yourself in the digital age. While the lines between these categories can sometimes blur as malware evolves, knowing the core characteristics of viruses (needs a host), worms (self-replicating and spreading independently), and trojans (disguises itself) empowers you to be more vigilant. Combine this knowledge with good cybersecurity practices – such as using reputable antivirus software, keeping your systems and software updated, being cautious of email attachments and links, and avoiding suspicious downloads – and you can significantly reduce your risk of falling victim to these pervasive threats. Stay informed, stay protected. What other types of cyber threats are you curious about?
Leave a Comment
Your email address will not be published.
4 Comments

Williams Thompson
May 3, 2025
Drones are getting so smart these days, I'm starting to feel like mine’s judging my driving from the sky. On a serious note though, amazing to see how far drone tech has come. Next stop: drone pizza delivery, I hope!

Williams Thompson
May 3, 2025
Drones are getting so smart these days, I'm starting to feel like mine’s judging my driving from the sky. On a serious note though, amazing to see how far drone tech has come. Next stop: drone pizza delivery, I hope!

Williams Thompson
May 3, 2025
Drones are getting so smart these days, I'm starting to feel like mine’s judging my driving from the sky. On a serious note though, amazing to see how far drone tech has come. Next stop: drone pizza delivery, I hope!

Williams Thompson
May 3, 2025
Drones are getting so smart these days, I'm starting to feel like mine’s judging my driving from the sky. On a serious note though, amazing to see how far drone tech has come. Next stop: drone pizza delivery, I hope!
Explore More Categories
Explore More Sub-Categories






















